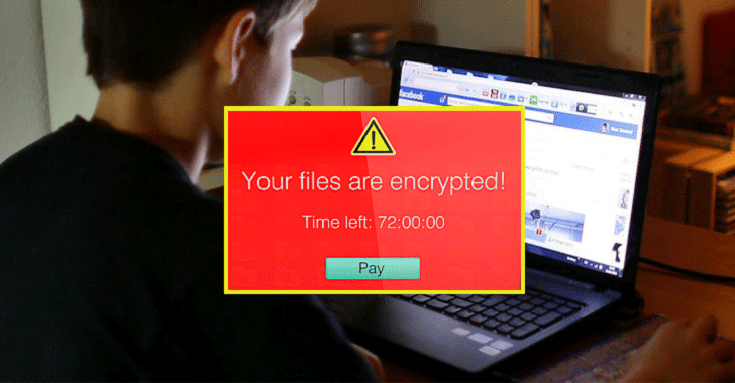
Beware of any type of image file sent on any type of social media platform, the likes of Facebook, LinkedIn etc even by your friends as you may get infected with Locky Ransomware. I told you in a previous article about a Facebook messenger campaign that was used to spread the same Locky Ransomware using infected .SVG image files. At that time, Facebook denied it was a real problem.
Now, the same Locky Ransomware may infect your computer if you click on inconspicuous .JPG files, i.e. images, so if you get an image sent by anyone on any type of social media platform, not just Facebook/LinkedIn, DO NOT CLICK ON IT. The Locky Ransomware is basically encrypting all the data on your device and unless you pay a ransom to the hacker, well, you’re out of luck and out of your 500 GB of cat-pictures, your life’s work so to speak.
The new .JPG malware spam campaign spreading through social media was revealed by an Israeli based security company, Check Point respectively. Cyber criminals managed to inject malware in .JPG /image files by discovering security issues in LinkedIn and Facebook which allow them to forcibly download an infected image file into the victim’s computer (sometimes you’ll have to click on the respective image in order to download it, do just don’t do that!).
The security flaws in LinkedIn and Facebook remain unpatched as I am writing this piece i.e. you’ve been warned. The Israeli based company refused to provide details with regard to the vulnerabilities, as the cyber attack is still ongoing and impacting social media platforms. Check Point reported their findings to Facebook and LinkedIn 2 months ago, in September, but the companies failed to patch the respective vulnerabilities. Be advised: do not open any type of unsolicited (image) file if it was automatically downloaded, especially ones with weird extensions, the likes of .SVG, HTA or JS.
Here’s a video demonstration of the attack:
Source: The Hacker News